Table of Content
The firewall configurations should be the most restrictive for this profile since these networks are the least secure. We use this profile for computers that connect to a private network, such as home or office. In private networks, the users are always behind a device and not directly exposed to the Internet. The DROP rule will instruct your server to block all types of connections from a specific IP address. By default, the NTP rule on the SecureAuth Identity Platform Appliance allows it to communicate with any NTP server for greater ease during the initial configuration. Post configuration security best practices recommend restricting communication to only trusted NTP servers on your network.

You’ll need to install the WHS Connector to every computer on your network that you want to connect with the server. It connects your computers to WHS, allows for automatic nightly backups, monitors computer network health, and enables you to remotely administer the server from your computer. You don’t need to leave a keyboard, monitor, or mouse to the server.
Ways to Implement a Server Firewall
A firewall throughput applies to hardware firewalls and usually offers a range of firewall throughputs to choose from. Entry-level to midrange hardware firewalls will have a throughput of roughly 500Mbps. For even more peace of mind, TP-Link’s router also comes with a lifetime warranty. You never need to worry when using it as you are protected should anything happen. There is also 24/7 technical support available, for free, so you are never in the dark or struggling. There’s a range of open-source software that you can install on this device, such as dd-wrt, FreeBSD, ClearOS, CentOS, OpenVPN, pfsense, and more, offering you fantastic customizing opportunities.
Power Packs are updates that add new features and provide fixes to known issues for Windows Home Server. When you open up WHS Console, you’re prompted to log into the server. There are a few other features here to like having the password remembered, password hint, and resetting the console.
Is It Worth Having A Firewall At Home?
They also enjoyed the fantastic visibility and customization of this, allowing you to tailor the system to your needs. You can adjust the firewall settings, enable deep packet inspection, enable QoS features, Intrusion Detection, create VLANs, and so much more! There are even features that allow you to manage other Unifi products that you have at home, such as WiFi access points and switches. Many hosting providers and Content Management Systems include options to set up specific types of firewalls.

This is always the case with the machine where you are creating the rule. Select ‘These IP addresses’ to state that the rule applies to the packets with an address specified in the list. You can later edit or remove any of the IP addresses in the list. Click Customize… and select to apply the rule to connections on all interfaces or chose one of the available interfaces listed in the box. This option blocks all network traffic that matches the firewall rule configuration. If a similar rule with ‘allow’ action is in place, then the block action has the priority unless otherwise is stated in the other rule.
Remote Coverage
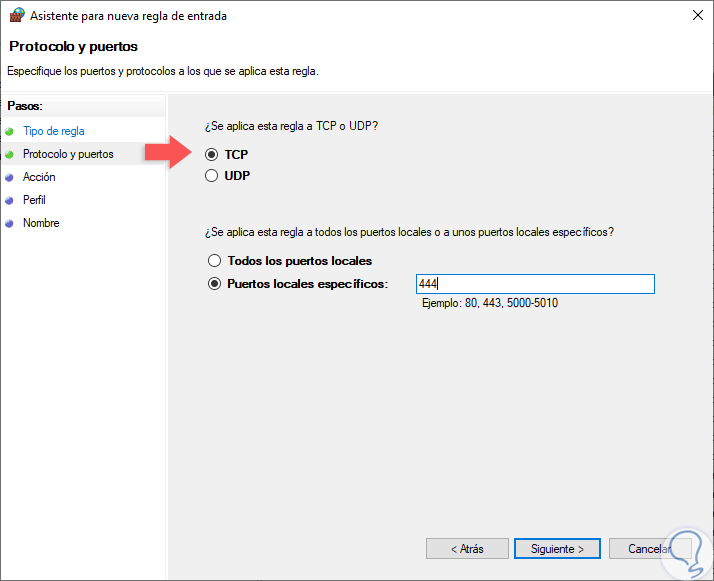
I will list the steps for creating an inbound rule and you can follow them in the same order when you want to create an outbound rule. It allows more inbound connections to allow for file sharing etc. The domain profile is selected automatically when connected to a network with a domain trusted by the local computer. This web site assumes some prior knowledge of forwarding or opening UDP and TCP protocol ports on your router or firewall. We cannot accept any liability for problems arising from the use of this web site or content.

Device monitoring will enable you to identify how many devices each network user accesses through the infrastructure and keep a close eye on it. Perhaps one of the most vital features of your firewall is how well it will protect you and disable any potential threats to your computer or devices. You want a firewall that will track and control all the applications and information on your network, both entering and exiting. While customers loved the router, some did note that it could be challenging to set up, especially for first-time users.
Windows
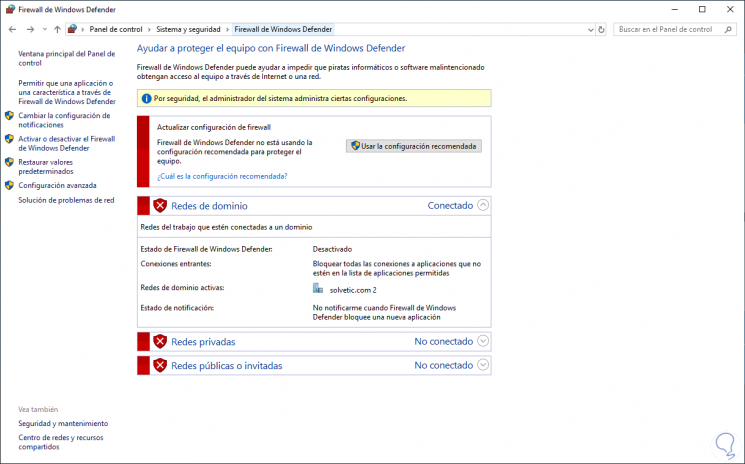
You can access the Windows Firewall with Advanced Security console in a few different ways. Whichever method you choose, it will open Windows Firewall MMC where you can make further firewall configurations for all profiles. Blocking your server doesn’t mean that no one will be able to access it.
These allow you much better control and visibility over your network as a whole and can be useful for those with children or others at home accessing the network and internet. They can also be advantageous for those running small businesses from their home and need to keep applications private for data protection purposes. Some firewalls will allow you to have some control over network users. You will be able to provide and prevent access on certain applications and even limit their use to functions on an application. These can then limit traffic entering your computer and risks to your network by only allowing approved applications to be used, almost like the ad blocker you might have on your internet browser.
Despite the small size, it is still a powerful firewall. The firewall comes with 4 Gigabit LAN ports and a Gigabit WAN port, making it the ideal choice for home or business. Like all firewalls, remote management and monitoring features are available through the Unifi Controller, also known as the Graphical User Interface . Alongside this, there are heaps of other features that allow you to create a safe space for your computer at home.
You can find the rule in the firewall console when you click on the Inbound rules option. Enabled rules have green checkmark icon while disabled are with grey icons. If you select ‘Any IP address’ in the remote IP addresses section, then the rule applies to the traffic coming from any IP address included in the list. Select ‘These IP addresses’ to insert the remote IP addresses to which the rule applies. You can customize the ICMP settings if you select ICMPv4 or ICMPv6 in the ‘Protocol type’ dropdown list. Once the window opens, go to Tools on the top right side, and locate the Windows Firewall with Advanced Securityoption toward the bottom of the list.
The difference between the two is the level of functionality available to the end-user, that is, the interface itself. The Windows Firewall is easier to use and more consumer-friendly. It is located in the Control Panel and allows you to perform basic firewall configurations. Hit the Windows key and find "firewall with Advanced Security." Select the first option as described below. Once the window of the firewall opens, go to the next step. Moving on, you’ll also need to change the value of HELPER_SSH_PORT to 7822, which is the default for SSH connections, as you might remember from the previous section.
It has the ability to backup 10 computers and restore them if needed. It acts as a media server, backup solution, data recovery, document management, and allows you to access what you need from anywhere there is a web connection. Using a personalized website address, it lets you securely download and upload your data files.
If you already own UniFi devices or are planning to add them to your collection, then this USG firewall is an excellent choice for you. It won’t cost you too much, customers love it, and the range of features can keep you busy for days. If you are unfortunate enough to have a Router that UPnP support is questionable, then the best thing you can do is disable UPnP on the Router and configure it manually. You can also disable, cut, copy, or delete the rule you selected. Make sure you highlight the correct rule to avoid changing firewall configurations for wrong rules.
IP tables enable you to grant or deny access to specific services and IP addresses. This provides you with full control over everything that goes in and out of your server, including Transmission Control Protocol and Secure Shell connections. In short, it’s going to be suitable for those who like to use the command line. The gateway device sits between the internet and local WiFi router, and its job is to route all traffic before it reaches the router. Here it can eliminate any prohibited or potentially threatening users, sites, or viruses, to ensure you remain safe. All devices connected to the device are protected and monitored thanks to advanced management and security features.

























